Configuration of a Built-in AD Connector
HelloID is a modern and secure cloud-based Identity & Access Management (IAM) solution. This solution serves as a bridge between local sources like your HR system and directories such as Active Directory (AD) or Azure AD for managing user accounts on a network, among other functionalities. HelloID acts as a mediator in this process. With the help of a handy built-in connector, you can seamlessly link AD and the cloud-based Azure AD to HelloID. In this blog, you will discover more about these connectors, their capabilities, and the benefits of integrating AD with HelloID.
What is Active Directory?
Active Directory (AD) is a proprietary technology developed by Microsoft, designed to help IT administrators in managing and safeguarding user accounts, systems, and other assets within a network. Additionally, Active Directory functions as a centralized point of access for various network-accessible resources.

Think of Active Directory as an extensive database within your network that houses all information regarding the organization's users and devices. It plays a key role in user authentication and ensures secure access to a wide range of resources, such as files, applications, IT infrastructure, and external devices like printers and scanners. Active Directory is generally hosted on an organization's internal network.
What is Azure AD?
Microsoft also provides a cloud-based version of its identity and access management service, known as Azure AD. This service not only facilitates secure access to external resources like Microsoft 365 and the Azure portal but also to a plethora of other SaaS solutions. Moreover, Azure AD extends secure access to internal resources, such as applications hosted on your company network. This applies to both off-the-shelf and custom-developed cloud applications.
Easy linking via built-in integrations
As the most widely used identity provider (IdP), Microsoft AD serves as the principal application that customers connect with HelloID. The built-in standard integrations are designed to make the linking of (Azure) AD to HelloID as simple, streamlined and rapid as possible.
Multiple built-in integrations are available in HelloID:
Integration of (Azure) AD as IdP: This integration allows users to log in to HelloID using (Azure) Active Directory and its available authentication features, including multi-factor authentication. To facilitate this, HelloID reads in all users, who then become available within HelloID for authentication and authorisation purposes. This integration is part of HelloID Access Management.
Integration of (Azure) AD using target connectors: With the help of target connectors, you can manage both users and authorisations within the IdP based on a source system, in an automated fashion. This integration is part of HelloID Provisioning.
A task catalog with standard tasks: You can easily perform various additional actions in (Azure) AD using standard tasks available through a catalog. This could involve creating additional groups on demand or activating/deactivating a specific user. This integration is aimed at self-service and helpdesk use.
In this article, we delve into integrating (Azure) Active Directory via target connectors. These connectors empower you to intricately manage identities within the IdP using HelloID. HelloID syncs with your source system, automating the read-write operations for user accounts and privileges across platforms. The swift and straightforward integration with (Azure) AD streamlines the way you handle identities in your organization and is often among the initial steps in a new HelloID setup. We provide a brief video tutorial explaining how to establish this link between HelloID and (Azure) AD.
Features of the connector
The Active Directory and Azure AD connectors come with an array of functionalities. We outline the most important ones below.
Creating and managing new users
With the help of the connector, HelloID automatically identifies identity management tasks for (Azure) AD. Based on individuals and employment statuses in a source system, HelloID secures the inflow and outflow processes towards your target systems. For instance, when an employee's contract ends, HelloID automatically deactivates their account, ensuring that former employees do not inadvertently maintain access to your systems. HelloID executes these processes automatically and consistently, while documenting everything in a clear audit trail.
Determining Roles and Assigning Permissions
HelloID's role blueprint plays a significant part in the processes surrounding the reading and writing of user accounts. You can configure this model to use attributes from the source system to determine a user's role. In this regard, HelloID acts as a mediator between a source system, like an HR system, and the target system, which in this case is AD or Azure AD.
Automating Identity Management
While identity supervision in (Azure) AD requires both expertise and the appropriate permissions, it's notably time-intensive. However, integrating AD with HelloID revolutionizes the landscape, fully automating identity management tasks. Another feature, the 'delegated forms', grants IT and HR staff the ability to kickstart identity management tasks without needing elevated permission levels. This prevents users from having unnecessarily high levels of access, thus reducing the risk of malicious activities. Delegated forms thereby enhance the digital security of your organization.
How Do You Configure an (Azure) AD Target System?
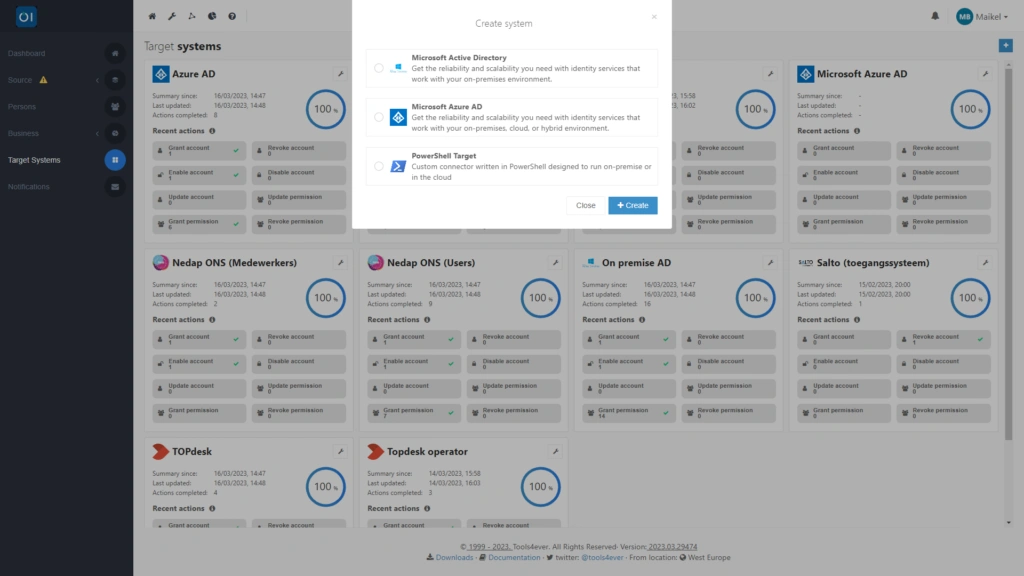
Setting up the target connector is quite straightforward. You can create a new link with an Active Directory or Azure AD within the 'Target Systems' tab by clicking on the plus icon.
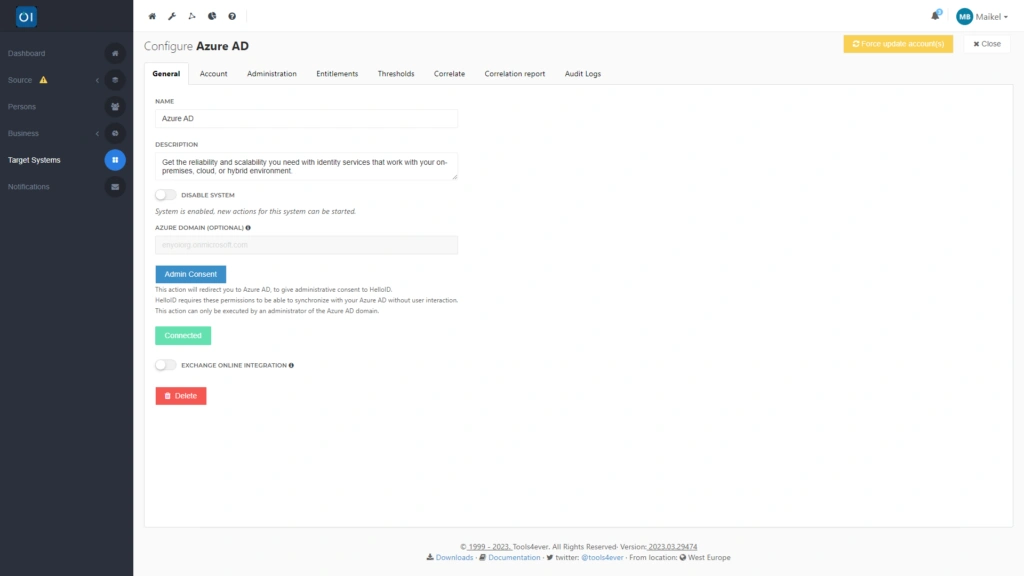
To modify an existing configuration, you click on the wrench icon next to the relevant Microsoft (Azure) AD. For keen observers, yes, it is indeed possible within HelloID to link multiple Active Directories or Azure ADs simultaneously. What's more, you can even add the same Active Directory multiple times with varying configurations. This can be useful, for example, if you want to manage and maintain privileged accounts through HelloID. For linking with Active Directory, you specify the AD domain, and for Azure AD, you specify your Azure tenant. To establish the actual connection, for an on-premise Active Directory, you'll need to select a HelloID Agent. For connecting with Azure AD, you log in to Microsoft with your admin account to grant what's known as 'Admin Consent.'
After making these correlations, you determine which data HelloID writes to which attributes in AD via the target mapping. This configuration process is similar to that for a source system. You will read more about configuring the naming conventions you wish to use for UPNs and email addresses in our next blog post. Also consider configuring HelloID's correlation function, which correlates data based on matching values. By using this correlation function, you ensure that existing accounts in a target system link to the correct individuals within HelloID. This is important, as an incorrect link could lead to various issues, such as the unintended creation of duplicate accounts or not deactivating an account after the employment relationship ends. More information about correlating data will be available soon.
Getting started with HelloID
Want to get started with connecting HelloID to Active Directory or Azure AD? In our documentation, you will find all the information you need to configure the AD connector of Azure AD connector. In the documentation, you will also find more information about the possibilities offered by these connectors. Do you have any questions, or would you like to spar with an expert about the use of the AD connector or Azure AD connector? Feel free to contact us.


Written by:
KaHo Man
KaHo, met 18 jaar ervaring in consultancy, is implementatie consultant in Identity & Access Management (IAM) bij Tools4ever. Met een solide basis in Hogere Informatica, is hij uitgegroeid tot een gerespecteerde mentor en trainer, die zijn kennis deelt met collega's en partners. KaHo's expertise strekt zich ook uit tot het geven van HelloID sales demo’s en technische intakes, uitvoeren van health checks, en het overzien van project reviews.