Installing and configuring a HelloID Agent
HelloID is a modern and secure cloud-based Identity & Access Management (IAM) solution. Do you want HelloID to communicate with local resources such as Active Directory or a database? This can be accomplished through communication via a HelloID agent. In this blog, we dive into the installation and configuration of agents for HelloID, and demonstrate how easy this process is.
What is HelloID?
The shift from on-site infrastructure to cloud-based systems presents its own set of hurdles. Questions regarding the management of user identification and controlling access to your platforms can be daunting, especially given the growing legal and regulatory demands in this domain. HelloID offers a solution, providing comprehensive answers to all your Identity & Access Management concerns.
Based on a source system, HelloID automates user and authorization management. The IAM platform also features a (delegated) self-service dashboard for handling optional requests and offers both simple and secure access to all your applications.
What role does a HelloID agent play?
HelloID comes with a default configuration that is entirely cloud-to-cloud. If your operations are fully cloud-based and you wish to implement HelloID in a standard manner within your cloud ecosystem, no agents are needed for the IAM solution. However, should you want HelloID to interface with on-site resources, an agent will be required.

The HelloID Agent consists of three streamlined Windows services that operate within your own organisation's network. These are the Directory Agent, Provisioning Agent and Service Automation Agent. These three Windows services enable communication with the various HelloID modules: HelloID Access Management, HelloID Provisioning and HelloID Service Automation. For specialized cloud-to-cloud applications, a Cloud Agent is also available.
What is the specific role of each HelloID agent?
Each agent serves a distinct function. Let's take a closer look at the individual agents and the roles they perform.
Directory Agent
The HelloID Directory Agent serves as HelloID's directory service and is responsible for on-site activities tied to the Access Management module of the IAM solution. For instance, it handles user authentication in HelloID by leveraging Active Directory as the Identity Provider. Additionally, the Directory Agent is responsible for synchronizing user accounts between Active Directory and HelloID.
Provisioning Agent
The HelloID Provisioning service is called the HelloID Provisioning Agent. This service performs on-premises tasks related to the HelloID Provisioning module. Its primary function is to pull data from source systems such as HR databases and Student Information Systems (SIS). Using this information, the service reads and writes user accounts as well as permissions into platforms such as Active Directory and G Suite.
Service Automation Agent
The third Windows service in the HelloID Agents suite is the HelloID Service Automation Agent. This service handles tasks associated with HelloID's Service Automation module. These tasks range from reading and modifying PowerShell data sources to importing Service Automation resources from GitHub, as well as running inline PowerShell scripts through delegated forms. By utilizing delegated forms, the service simplifies user interactions and reduces the permission levels needed to complete tasks. Offering 64-bit support, the Service Automation Agent is capable of loading 64-bit PowerShell modules, including those for Azure and Exchange Online.
Cloud Agent
The standard HelloID Agent operates as an on-premises application within your organisation's network. However, more entities transition entirely to cloud-based operations yet still want to execute PowerShell actions for their use case. A number of functionalities of HelloID therefore also support the HelloID Cloud Agent. Hosted on Tools4ever servers, this specialized agent allows for the implementation of custom PowerShell actions in your cloud environment. For instance, it enables the execution of PowerShell actions via delegated forms and provides access to PowerShell data sources. The Cloud Agent is primarily designed for making API calls to cloud-based web services. Due to security considerations, not all PowerShell actions are permitted in the cloud, and the Cloud Agent cannot perform actions in on-premises environments.
Creating a HelloID Agent Pool
After creating an Agent Pool, you can begin the installation and configuration of one or more agents. To be operational, each Agent Pool must include at least one HelloID Agent.
To install an agent, select the 'Install agent' option located in the 'Agents' section of the dashboard. A setup wizard will then walk you through the installation steps. This wizard will provide you with an installation file that you execute on the server where you wish to install the agent. The installation process is made user-friendly and intuitive thanks to the wizard. Moreover, the dashboard offers management options for the agent, allowing you to restart, manage or uninstall the agent as needed.
Can I securely connect HelloID to my local environment?
Acting as a "broker", the HelloID Agent facilitates data exchange and performs local actions. Given that the agent communicates over the Internet, security is paramount. To that end, all communications are conducted via HTTPS, employing TLS 1.2 and AES256 encryption to ensure a secure data transfer.
A verification process is in place to ensure that only the authorized instance of the agent is trusted. For instance, when installing the agent, HelloID generates a one-time passcode (OTP) ticket number. This number is single-use and expires 10 minutes after being generated. Utilizing a combination of the OTP, portal URL and the agent's unique identifier (GUID), HelloID produces a shared certificate. This certificate serves to authenticate any communication attempts between HelloID and the agent. Without a valid certificate, communication is impossible.
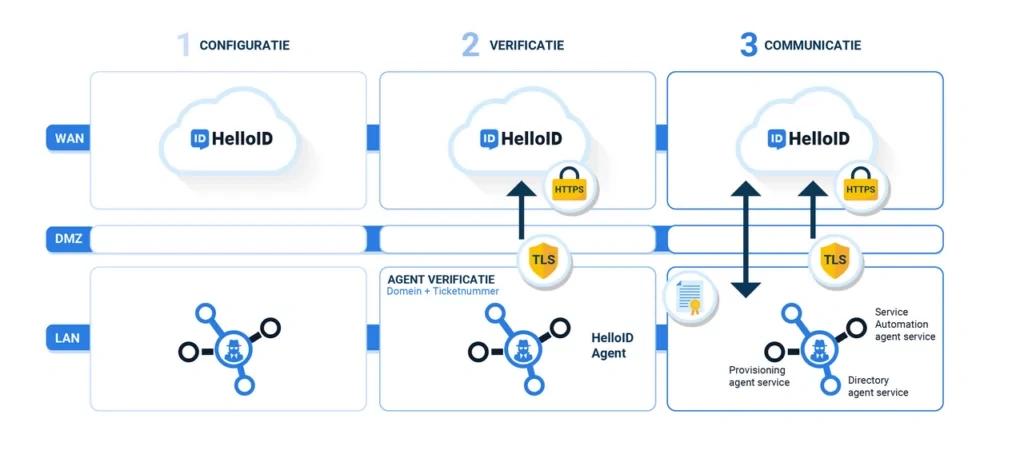
Moreover, HelloID employs a one-way communication model. Communication is strictly unidirectional, flowing from the local network to the HelloID portal, but never in reverse. The agent can only carry out actions pre-arranged by the HelloID portal and is not capable of independently sending commands to the portal. Additionally, the agent will only execute requests originating from the IP address used during its authentication process. As a result, there's no need to open a port in your firewall or make special configurations in your demilitarized zone (DMZ).
Would you like more information about HelloID's digital security?
Read our HelloID Security-whitepaper
Getting started
Interested in starting your journey with HelloID and its agents? Our specialists are eager to guide you. They'll happily assist you in identifying the agents that align with your specific needs and help you establish Agent Pools, as well as help you utilize the HelloID Cloud Agent. Intrigued by what's possible or have any questions? Feel free to ask away.

Written by:
KaHo Man
KaHo, met 18 jaar ervaring in consultancy, is implementatie consultant in Identity & Access Management (IAM) bij Tools4ever. Met een solide basis in Hogere Informatica, is hij uitgegroeid tot een gerespecteerde mentor en trainer, die zijn kennis deelt met collega's en partners. KaHo's expertise strekt zich ook uit tot het geven van HelloID sales demo’s en technische intakes, uitvoeren van health checks, en het overzien van project reviews.
Others also viewed
 From A to IAM
From A to IAM
- Product and technology
Why do you need an IAM solution?
29 August 2022
 From A to IAM
From A to IAM
- Product and technology
How a Service Automation Solution Helps Your Organisation
31 October 2022
 From A to IAM
From A to IAM
- Product and technology
How a User Provisioning Solution Helps Your Organisation
27 September 2022
