
Multi-Factor Authentication (MFA)
What is Multi-Factor Authentication (MFA)?
In short, Multi-Factor Authentication (MFA) is an authentication method where the online user must successfully complete two or more steps to gain access. This type of authentication is also known as Two-Factor Authentication (2FA). While 'two-factor authentication' remains a popular term, MFA has increasingly become the overarching term.
How Does MFA Work?
The first step is entering a username and password, which is the most common form of authentication today. Since the creation of individual user accounts for computer and application access, usernames and passwords have been the norm. The password is the most popular and one of the most used security measures, but often also the most vulnerable. For example, in the United States, an email address is linked to an average of 130 different user accounts [i]. Two-thirds of users even use the same password for multiple accounts, which can cause major data breaches [ii].
The second step is that in addition to entering your login name and password, you need to enter a second key to be able to log in. Some possible options include: receiving an SMS code, receiving a login request in a linked app on your smartphone, or entering a generated code. Only this combination ensures access.
Nowadays, cards with PIN can replace the login screen. You scan your card (step 1) and then enter a PIN/password (step 2).
A bank card combined with a PIN code is a simple example of two-factor authentication. When one of the crucial components is missing (bank card or PIN code), access to the account cannot be obtained.
These examples show how MFA is an essential part of our daily interactions with technology and how it helps keep our data and information secure.
Why is MFA Important?
In the digital age we live in, securing data and information is crucial. Cyberattacks and data breaches are commonplace, and the consequences can be devastating for both individuals and organizations. This is where MFA (Multi-Factor Authentication) comes in.
MFA plays a vital role in strengthening security by adding an extra layer of protection. While traditional security methods, such as using a single password, can be vulnerable to attacks, MFA makes it much harder for unauthorized persons to gain access. Even if a password is compromised, MFA provides an additional barrier that must be overcome.
Furthermore, MFA helps counteract the human factor in security risks. People tend to use simple, easy-to-remember passwords and often reuse them across multiple accounts. This makes them vulnerable to attacks. MFA reduces this risk by requiring users to provide a second form of authentication.
Additionally, MFA is also important for regulatory purposes. Many industries and regions have strict data security regulations and require the use of MFA. By implementing MFA, organizations can comply with these regulations and avoid potential fines or sanctions.
In short, MFA is important because it is a powerful, effective way to enhance data and information security, reduce the human factor in security risks, and comply with regulatory requirements. In a world where cyber threats are becoming increasingly sophisticated, MFA is not a luxury but a necessity.
The 5 Authentication Factors
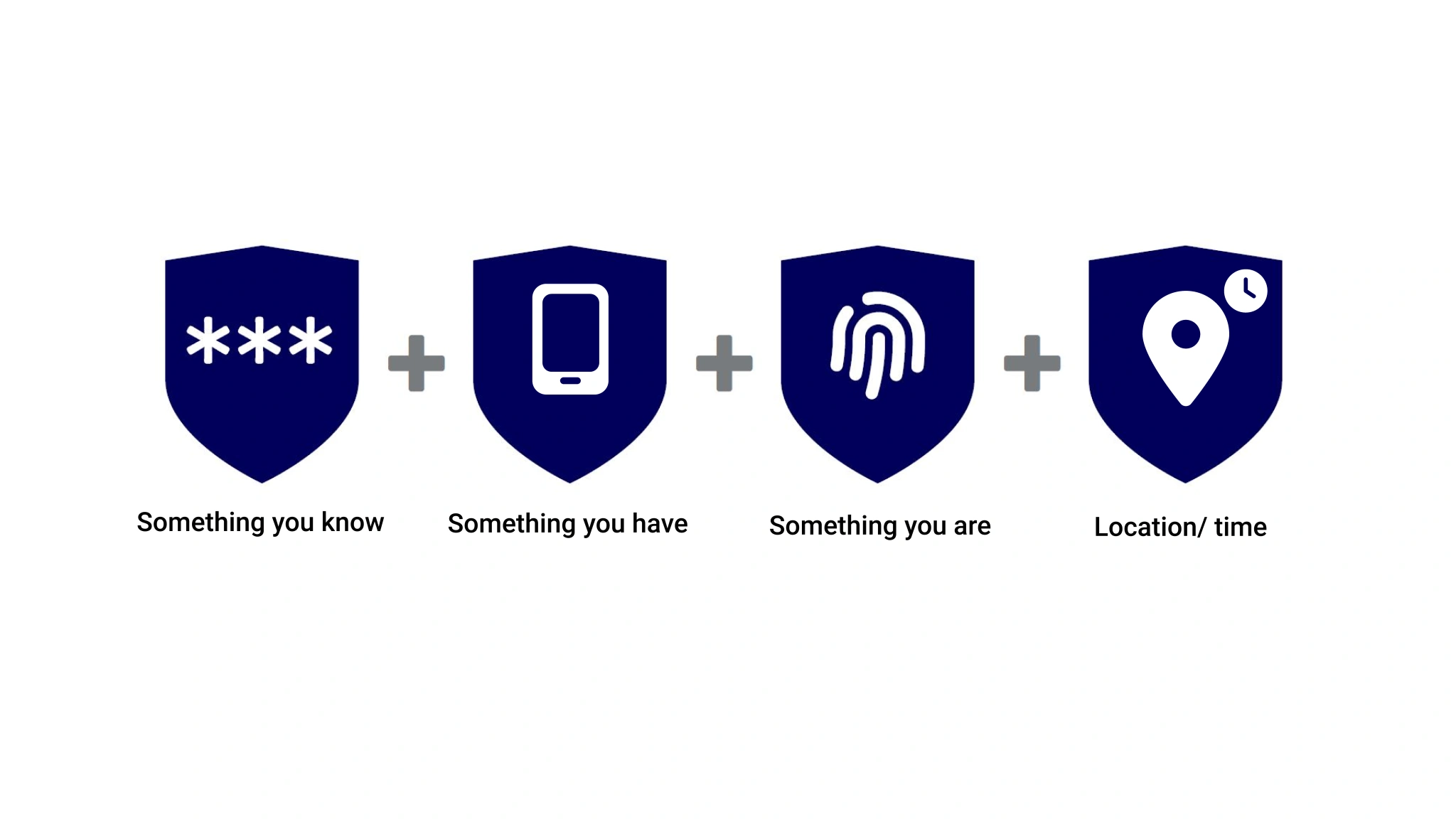
We can divide authentication means into five categories (or factors): something you know, something you are, something you have, location, and time. When it comes to security, each factor has different properties.
1. Something you know - This first factor is familiar to us all: the username and password. Security questions also fall under this category. Combining a username and password with a security question is still considered single-factor authentication because they both fall into this category.
2. Something you have - Includes items such as key cards and hardware tokens. One-time passwords sent via SMS or email to users' mobile phones are increasingly classified under this factor. The use of mobile devices helps combat the risk of losing physical items. In some systems, the user's device itself acts as a factor in this category, once it has been marked as a "trusted device".
3. Something you are - This authentication factor includes all biometric data that can serve as credentials. Examples are fingerprints, facial recognition, or iris scans. This type of authentication has become increasingly popular with mobile devices that have built-in fingerprint scanners and facial recognition. These means are easy to use. After all, you always have your fingerprint with you, and it's not something you can easily lose.
4. Location - Refers to the geographical or network restrictions that can be added to authentication methods for extra security. For example, users may only access an application when they are within the company network or in a specific country.
5. Time - Refers to any restrictions that can be added to keep authentication within a certain
range of hours. Time-based factors provide security by allowing users to log in only within a specific period - for example, between 09:00 and 17:00.
Additionally, there are MFA methods that use communication channels, such as SMS or email codes, where a one-time code is sent to the user's phone or email address, or push notifications, where the user receives a notification on a trusted device to confirm a login attempt.
Each MFA method has its own advantages and disadvantages, and the choice of a particular method depends on various factors, such as the nature of the data being protected, the technical skills of the users, and the cost of implementation.
MFA in Daily Use
Let's take the example of the bank card again to outline how these five authentication means are used in daily life.
When you withdraw money, it can only be done by authenticating yourself. The bank card serves as 'something you have' and your PIN code as 'something you know'. Of course, other conditions can be enforced instead of your PIN code, such as a fingerprint 'something you are'. If your bank limits the number of ATMs you have access to, a location factor is in effect. The number of transactions in one day enforces a time factor.
Other Examples of MFA in Action
MFA, or Multi-Factor Authentication, is a security method we often encounter in our daily lives, sometimes without even realizing it. Here are some examples of MFA in action:
Online Banking: When you log into your online bank account, you are often asked to enter a one-time code sent to your mobile phone in addition to your username and password. This is a form of MFA, where the second factor is the one-time code you receive.
Social Media: Platforms like Facebook and Instagram offer MFA options for added security. After entering your password, you may be asked to enter a code sent to your phone, or to confirm a notification on a trusted device.
Workplace Security: In many companies, MFA is a standard part of security protocols. Employees might be asked to use a fingerprint or a smart card in addition to entering their password to access their workstations or certain applications.
Email Providers: Services like Gmail and Outlook offer MFA options to secure users' email accounts. In addition to the password, you may be asked to use a second factor, such as a code sent to your phone, or confirming a prompt on a trusted device.
Why is MFA the Solution?
There are many benefits associated with Multi-Factor Authentication, we have outlined the most important ones below:
Better security: Not only because it prevents password theft, but also because logging in with just a username and password is vulnerable to brute-force attacks or social engineering/social hacking.
Simplification of the login procedure: You might think that MFA makes the login process for accounts more complicated. However, thanks to the extra security of MFA, companies can use more advanced login options, such as Single Sign-On, single login. Replacing the login screen with a card greatly simplifies the login procedure. Users only need to enter a PIN or password afterward.
A step towards compliance: The GDPR requires you to set up a system that optimizes the control of certain data. This is especially true when protecting sensitive data such as personally identifiable information or financial data. That means MFA is a necessary step for compliance.
An essential part of cybersecurity: With the increase in cloud applications, there is also an increased risk of data breaches. MFA is one of the best security measures to protect your organization, users, and sensitive data.
How to Implement MFA in Your Organization
Implementing MFA in your organization can significantly improve security. Here are some steps to help you in this process:
Evaluate your needs: Determine which systems and data need protection and who should have access to them. Also, consider the technical skills of your users and the potential
impact on the user experience.
Choose the right MFA method: As discussed earlier, there are various MFA methods available, each with their own advantages and disadvantages. Choose the method that best fits your needs and circumstances. This may be a combination of methods, depending on the different roles and access levels within your organization.
Find a reliable MFA provider: There are many providers that offer MFA solutions. Look for a provider that offers a robust, secure, and user-friendly solution and that provides good customer service and technical support.
Implement the MFA solution: This can be a complex process, depending on the size and complexity of your organization. It may be useful to enlist the help of IT professionals. Ensure that the implementation is thoroughly tested before it is fully rolled out.
Train your employees: Ensure that all users understand what MFA is, why it's important, and how to use it. This can be achieved through training sessions, manuals, and ongoing support.
Monitor and update your MFA solution: After implementation, it's important to continue monitoring the effectiveness of your MFA solution and update it as necessary. This may involve adjusting the methods used, adding new users, or changing access levels.
Implementing MFA is an important step in enhancing the security of your organization. While it may take some time and resources, the improved security and peace of mind it provides are well worth the investment.
Interested in implementing MFA in your organization? Discover how our HelloID solution can help you secure your data and improve your identity and access management.
Conclusion
In an era where cyberattacks and data breaches are increasingly common, implementing Multi-Factor Authentication (MFA) is not a luxury, but a necessity. MFA adds an extra layer of security to your systems and data, making it significantly harder for unauthorized persons to gain access.
There are various MFA methods available, each with their own advantages and disadvantages, and the choice of a specific method depends on your particular needs and circumstances. It's important to carefully evaluate your needs, choose the right MFA method, find a reliable MFA provider, carefully implement the MFA solution, and train your employees on its use.
While implementing MFA may take some time and resources, the improved security and peace of mind it provides are more than worth the investment. In the fight against cybercrime, MFA is a powerful weapon that can help protect your organization.
Product Flyer Video HelloID Access Management Download HelloID whitepaper
Not a Tools4ever customer yet but curious about the possibilities?
Make an appointment