Writing data back to the source system
HelloID is an Identity & Access Management (IAM) solution that acts as a mediator between your source system (such as an HR system) and target systems (including Active Directory (AD), Azure AD or Google Workspace). Previously, we outlined how to import HR data and map it to your source information. In this blog post, we delve into the process of writing data back to your HR system, exploring the options available and key considerations to keep in mind.
You can link various source systems to HelloID. The IAM solution primarily uses a source system for importing HR data. HelloID needs this information to manage both user accounts and rights. However, in certain cases, you might also want to write data from HelloID b/blog/2023/import-source-data-from-an-hr-system/ack to your HR system. HelloID especially enriches data during the onboarding process. You often want to relay these enriched data back to your source system. For instance, think of an email address that HelloID creates in (Azure) AD or Google Workspace based on data from your source system.
Getting started with writing data back to the source system
Writing data to your source system is done using a target connector. In this case, you configure your HR system not just as a source, but also as a target system. A connection like this is available for every popular HR system (that technically supports it). For this example, we will assume AFAS as the HR system. If you are using a different HR system, the approach may vary slightly in some aspects.
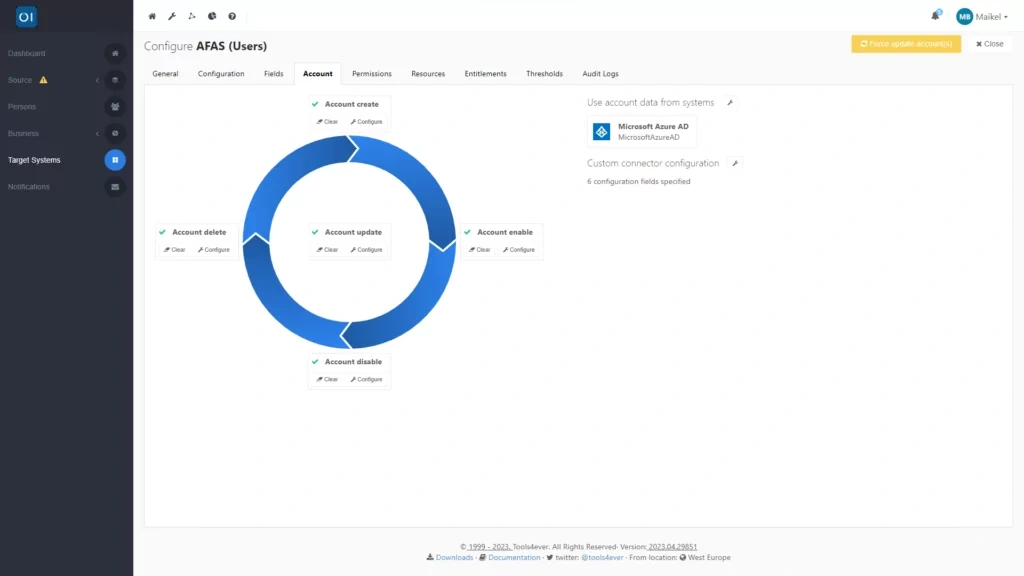
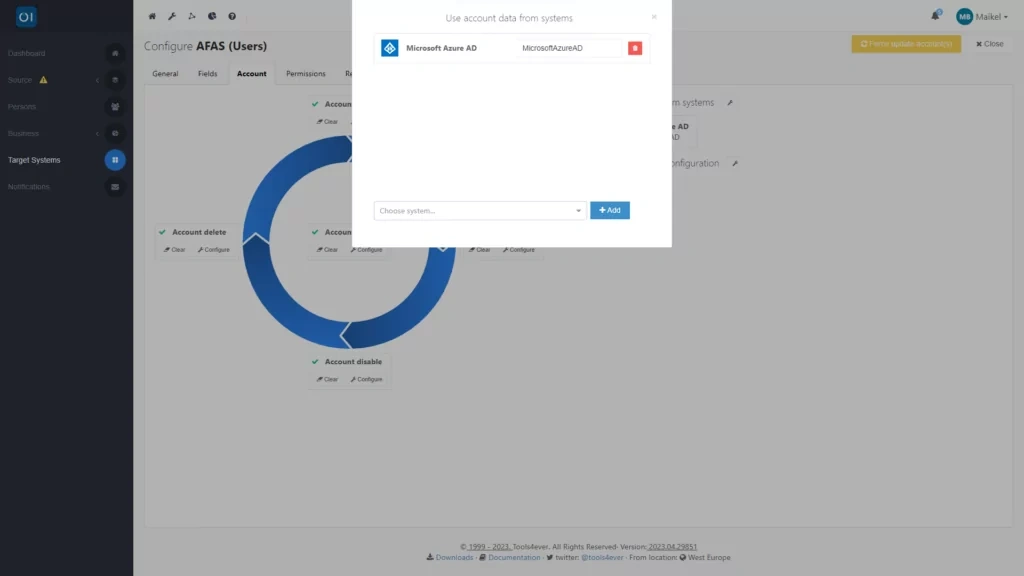
In this scenario, we are focusing on writing back the email address and User Principal Name (UPN) of a user to the AFAS system. The HR system stores a business email based on individual records and a UPN associated with the InSite account. We will set up separate target connectors for each field, enabling HelloID to accurately return this information to AFAS. This process is managed through HelloID's Provisioning dashboard, where you will establish a new target connector for each field under the Target Systems section.
Importing and configuring target connectors
In HelloID's public GitHub repository, you can find target connectors for all popular HR systems, including AFAS. Note that in the case of AFAS, there are two target connectors available for writing back data to the source system: one for individuals and one for users. Therefore, make sure to choose the correct connectors when configuring both fields.
From the repository, you will download several scripts, which you then load into HelloID. The exact scripts depend on the target connector you are configuring. For the AFAS target connector for individuals, the following scripts are involved:
ps1 for creating new data
ps1 for updating existing data
json for creating configuration options and adjusting the configuration of the connector
For the AFAS target connector for users, in addition to the above scripts, the following are also required:
ps1 for deleting accounts
ps1 for deactivating accounts
ps1 for activating accounts
Don't be daunted by the term 'scripts', as all you need to do is copy the contents of the files and paste them into HelloID. This is done by clicking the ‘Configure’ button for each account lifecycle action and then pasting the corresponding PowerShell script there. In the near future, HelloID Provisioning – similar to the template integration of delegated forms in HelloID Service Automation – will directly integrate with GitHub. This means there will be no need for copying and pasting, as connectors can be directly searched for and imported from within HelloID.
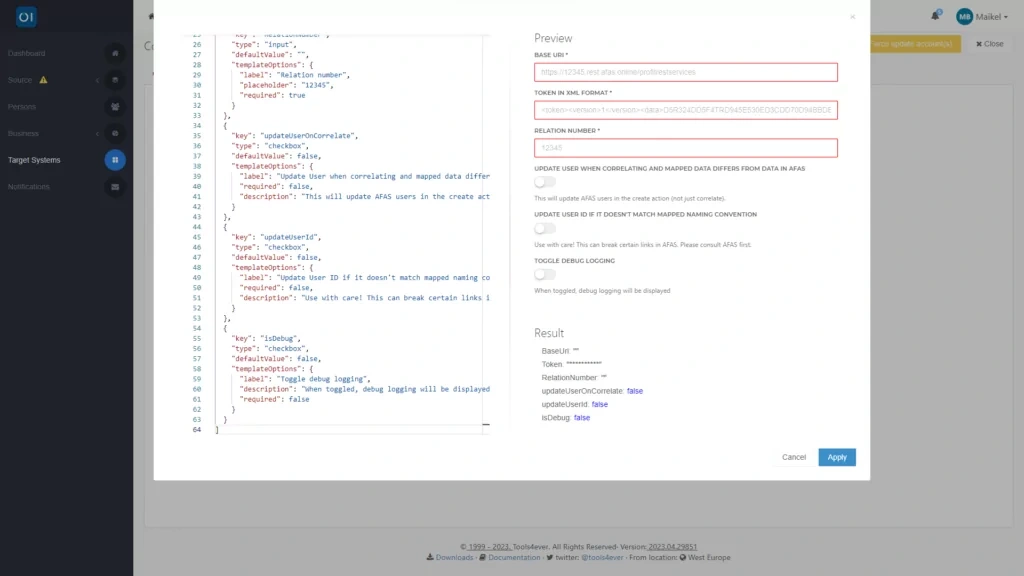
After loading the scripts, you can start configuring the connector. With the help of configuration.json, you have added configuration options to the connector dashboard.
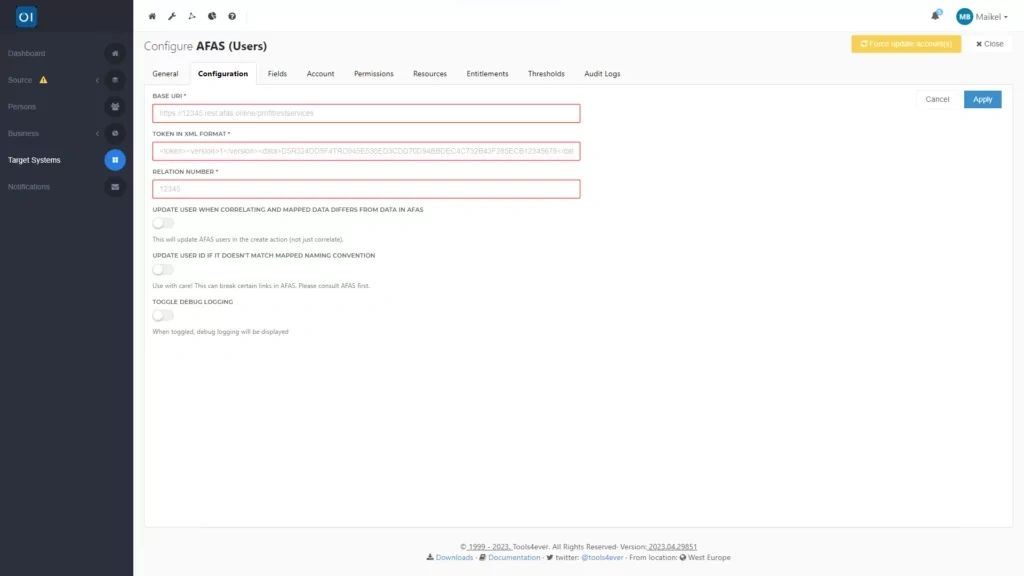
This means you can configure key settings through the graphical interface. On this tab, you will fill in details such as a URL to access the Profit Rest services and a token in XML format.
Enforcing the sequence of execution
If HelloID creates an account in, say, AD or Azure AD, and thereby generates a UPN, you will want to ensure that HelloID returns this UPN to your HR system. This information is used for SSO in AFAS. To achieve this, you need to connect the target connector to your directory system and establish a dependency. This step ensures that everything happens in the right order. It ensures HelloID sends the UPN to the target connector after it is created, which then writes this data back to the HR system.
Testing the target connector
Want to test how your target connectors are working? A 'dry run' is the way to go. Essentially, this means HelloID simulates the process without actually performing any actions, allowing you to test the connector easily and without risk. The connector will gather all the necessary data but will not write it back to your HR system. To do a dry run, simply activate this option in the connector’s settings.

Adding business rules
Once your target connectors are set up, you can move on to configuring business rules. These rules determine the actions HelloID carries out. With the target connectors in place, you can now include writing data back to your HR system, in this case AFAS, as part of these actions.

Getting started
If you are keen to begin writing data back to your source system, why not watch our brief tutorial video? It provides clear guidance on setting up the target connectors you will need. And if you have any questions, feel free to reach out to us. Our team is always ready to offer expert advice and support.

Written by:
KaHo Man
KaHo, met 18 jaar ervaring in consultancy, is implementatie consultant in Identity & Access Management (IAM) bij Tools4ever. Met een solide basis in Hogere Informatica, is hij uitgegroeid tot een gerespecteerde mentor en trainer, die zijn kennis deelt met collega's en partners. KaHo's expertise strekt zich ook uit tot het geven van HelloID sales demo’s en technische intakes, uitvoeren van health checks, en het overzien van project reviews.