USE CASE
Secure Cloud Access
Secure remote work, based on a cloud-based, automated and role-driven account and access management system.

CHALLENGE
How Can You Work Remotely in the Cloud, in a Secure and User-Friendly Way?
We are working remotely more and more often, storing data in the cloud, using cloud-based applications, and doing so on the go from a variety of different devices. Not only should an organisation’s own employees have access to data, but the same goes for their flexible workers, clients and partners. In such a widely dispersed and complex digital landscape, information security is crucial, but how can we set this up effectively?
NECESSITIES
Features
HOW IT WORKS
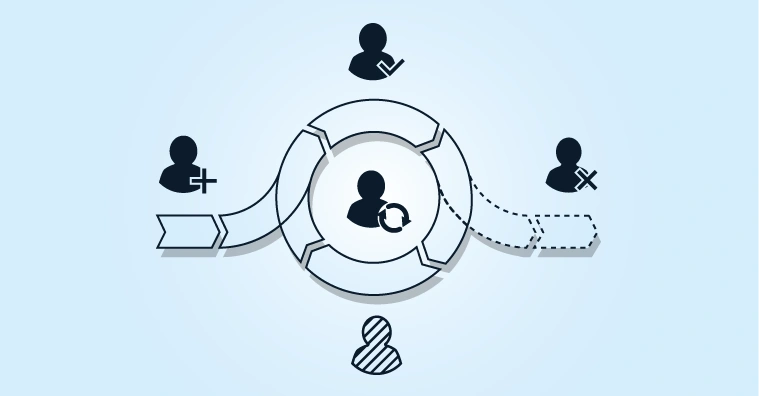
How Do We Establish a Remote and Cloud-Ready Identity and Access Management System?
6 steps that can each be configured using low-code or no-code solutions
Source system: Integration of HelloID with source systems such as HR, SIS and/or scheduling systems. This way, changes in the source data are automatically available in HelloID.
People: Conversion of data about people/roles from source systems to a common representation within HelloID using an ‘identity vault’.
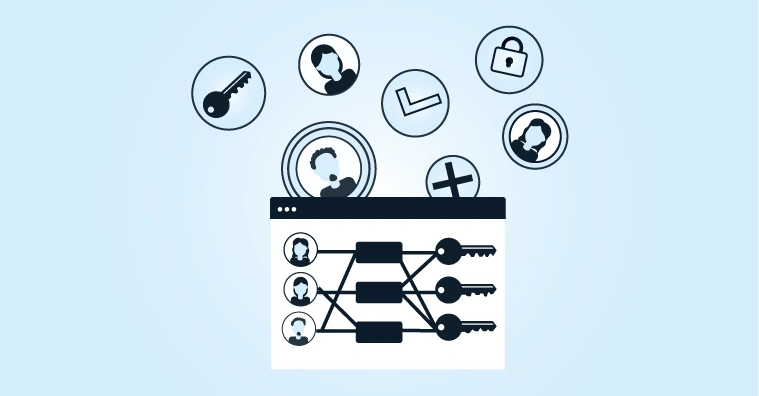
Business rules: Determining rules that determine which roles are granted which types of accounts and access rights, and under what conditions.
Target systems: Linking HelloID to on-premises and/or cloud-based applications. This can be executed step by step per application.
Access management: Set up access procedures, such as Single Sign-On (SSO) and Multi-Factor Authentication (MFA), in conjunction with — for example — Active Directory.
Reporting and auditing: Configuring standard and client-specific reports and monitoring functions for analysis and audits.