USE CASE
Improved Organisational Security
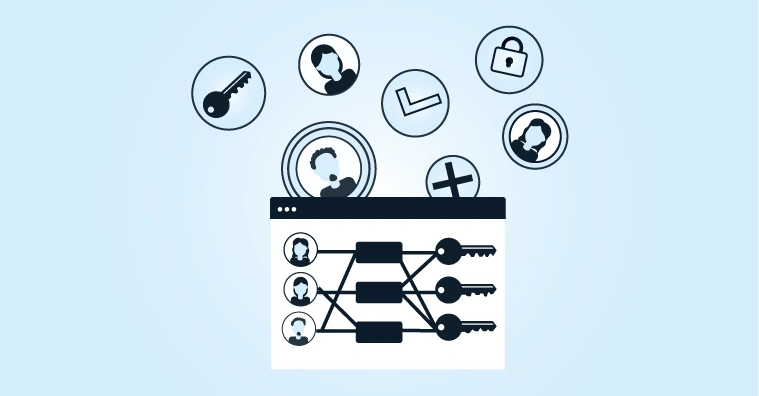
A role-based Identity and Access Management system that aligns with the 'least privilege' concept and is at the heart of a zero-trust architecture.

CHALLENGE
How Do You Migrate to a Future-Oriented Security Approach?
Traditional organisational security is based on well-defined security perimeters. The full focus is on ensuring good security when it comes to corporate network access, but once access is granted, it is assumed that connected users and devices are trustworthy. Now that remote working is becoming more common and not only staff but also contractors, customers and partners need to have access, a fundamentally different security approach is required.
NECESSITIES
Features
HOW IT WORKS
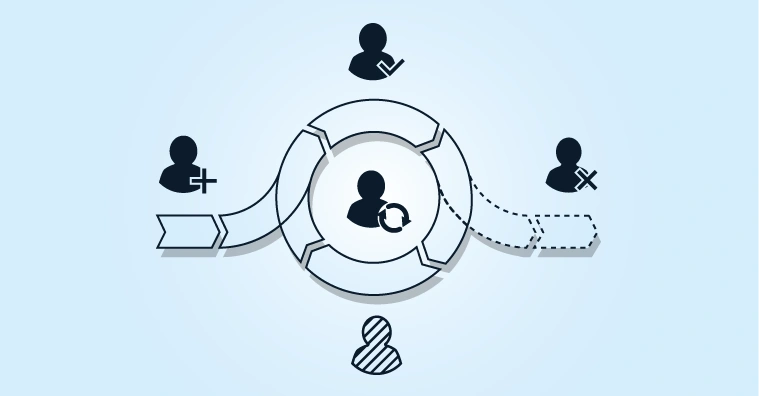
How We Establish a Zero-Trust Ready Identity and Access Management System
7 steps that can each be configured using low-code or no-code solutions
Source system: Integration of HelloID with source systems such as HR, SIS and/or scheduling systems. This way, changes in the source data are automatically available in HelloID.
People: Conversion of data about people/roles from source systems to a common representation within HelloID using an ‘identity vault’.
Business rules: Determining rules that determine which roles are granted which types of accounts and access rights, and under what conditions.
Target systems: Linking HelloID to on-premises and/or cloud-based applications. This can be executed step by step per application.
Service processes: Automating processes, including online approval flows and activation in target systems. This can be carried out step by step for each process.
Access management: Set up access procedures, such as Single Sign-On (SSO) and Multi-Factor Authentication (MFA), in conjunction with — for example — Active Directory.
Reporting and auditing: Configuring standard and client-specific reports and monitoring functions for analysis and audits.